cross-posted from: https://slrpnk.net/post/8481443
I am currently investigating and reverse engineering free VPNs for a master thesis, and just came across something I thought I'd share. Not sure if I'll name-drop the VPN that this code is from, but it's not the one mentioned within the hardcoded links... Nor do I encourage visiting any of the links in the screenshot.
I'm sharing this as a warning as to never use free vpns! They are most often the opposite of what they promise to be. (by free I do not mean the free versions of premium services). But either way; be careful about your VPN choice, as they have access to a lot of sensitive data. I'm sure most peeps here know of this already, but next time you hear someone using a free vpn, let them know...
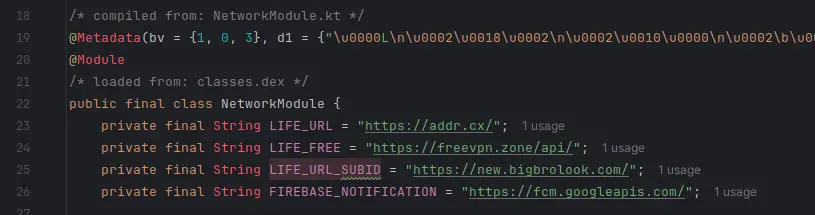
This first image/code was sitting inside a file called NetworkModule, with some hella weird external links.
- addrDOTcx, seems to have been linked to malware? Comes up flagged as malicious a few times on VirusTotal.
- freevpnDOTzone, seems to be another free possible malicious VPN service, might investigate this one later.
- bigbrolookDOTcom, seems to longer be a registered domain. But wtf? Was this VPN service linked to p*rn??
IMAGE HERE; Don't visit these links unless you know what you're doing.
Furthermore, there is this interesting find; Now I am no expert coder, frankly quite the amateur. But does the below code really mean what I think it does? Seems like it could be creating a fake connection?

Is used once here;
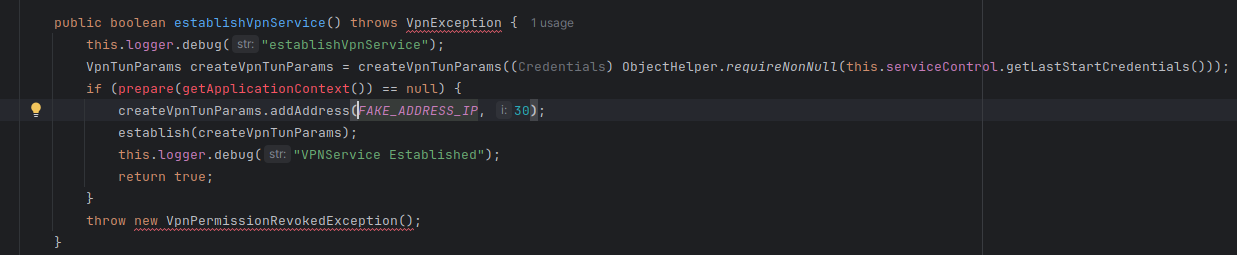
Stay safe 🌻
edit: formatting


