this post was submitted on 20 Feb 2024
1127 points (97.2% liked)
Microblog Memes
5699 readers
2303 users here now
A place to share screenshots of Microblog posts, whether from Mastodon, tumblr, ~~Twitter~~ X, KBin, Threads or elsewhere.
Created as an evolution of White People Twitter and other tweet-capture subreddits.
Rules:
- Please put at least one word relevant to the post in the post title.
- Be nice.
- No advertising, brand promotion or guerilla marketing.
- Posters are encouraged to link to the toot or tweet etc in the description of posts.
Related communities:
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
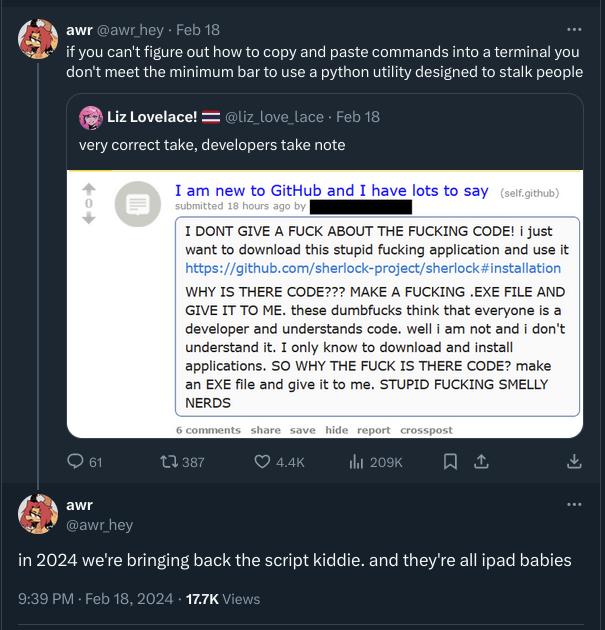
This is not a standard tool. This is an offensive security (aka hacking tool).
The hacking community does not want people like the one in the post.
All of this still applies to any open source project
There is one core difference. In regular open source projects, lack of layman accessibility is considered a bug.
For offensive security tools such as in OP's post, it simply isn't a consideration because the audience for these tools are not laymen, therefore they aren't designed with laymen in mind.
In fact there's something of an incentive to keep laymen out because people just hitting random buttons without serious consideration of what they are doing can land people in jail.
They're designed with the offensive security community in mind, of which even the most rookie members think nothing of firing up terminal and entering some nifty commands.
I'm talking more open source in general and scraping tools aren't 'hacking'.
Sherlock is an Open Source Intelligence (OSINT) tool. It is specifically made to gather information on a target, which is always step 1 of an attack.
We can agree to disagree on whether it constitutes an attack tool, however it is clearly made with red teamers in mind.
So I guess ping is a hacking tool now too huh?
There isn't a fuckdamn single drop of intellectual honesty in any of these comments.
Does ping have the potential to lead you almost directly to a potential attack path? Because Sherlock can.
Well what the fuck would I know? I've only been a pentester/red teamer for 8 fucking years.
Hey, wanna know what's by far the most useful tool in a red teamer/attacker's arsenal?
A fucking notepad!
Because the process isn't about tapping a few fucking buttons and you've hacked into the mainframe. You gather information. You make links. You poke and prod at stuff. You try to keep a low profile while you also try to figure out where your objective is. Then, and only then, you make a final plan and go for the objective.