I’m unique :) this ain’t great
Privacy
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn't great, if contents of the website are behind a paywall maybe copy them into the post
- Don't promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
much thanks to @gary_host_laptop for the logo design :)
its ok if your fingerprint changes on every browser startup
...as long as you are blocking tracking cookies, and aren't on a session with a website that's tracking you.
Otherwise, you just have a nice unique hash in your cookies. A password manager could help here.
If you have canvas randomisation turned on (firefox) you'll always be unique but also not traceable between sessions.
Yup, canvas is heavily weighted in this test based on the results.
How do you turn on canvas randomisation in Firefox? I can't seem to find anything about it.
I found this in about:config, defaults to true apparently: privacy.resistFingerprinting.randomDataOnCanvasExtract
But you have to enable privacy.resistFingerprinting for it to work first. I enabled that and now the EFF test says "randomized" for the hashes but also Lemmy went from dark to light theme somehow.
privacy.resistFingerprinting breaks a lot more than just themes. Many of the weird problems reported in Firefox (and forks) are just from enabling it.
It has some pros but also TONNES of cons. Everything from a completely blank page to wrong timestamps to poor textures and so much more. Sometimes you will be flagged as a bot and prompted with literally infinite puzzles, thus effectively banning you from a website.
Some of these problems get fixed but new ones also get born. I personally use it but I also expect breakage and worse performance.
With browser settings that actually let me use the internet in a way that's not overly cumbersome and annoying, I get 16bits or something and a "nearly unique fingerprint"
Block any and all ads, then it doesn't matter that they have your data if they can't make money off of it (they still will do that by creating data aggregates but you can't control that)
"Your browser fingerprint appears to be unique among the 183,614 tested in the past 45 days.
Currently, we estimate that your browser has a fingerprint that conveys at least 17.49 bits of identifying information."
Chat am I cooked?
Same result here. I'm using Gnome-web, which is already pretty niche, so that probably really lowers my score.
Am I wrong to assume trying to blend in is a worse and contradictory strategy than trying to actively protect yourself from tracking?
If you want to not be unique, use default setting chrome without adblock. Your browser will look just like anybody else's, but they will literally know who you are.
On the opposite side of the spectrum, you lock everything down and spike as a very special browser and... that's all they know.
Privacy vs. anonymity
Right. The question is whether they can attach what they know to an identity. Depends on your threat model which goal you need to achieve.
But then they can know a lot more since they don't even need to drop a cookie to track you. But that's a different threat model.
Despite having strong protection according to these results, I always get unique fingerprinting from them. Which is scary.
Edit: Now I tried Tor on my desktop and got:
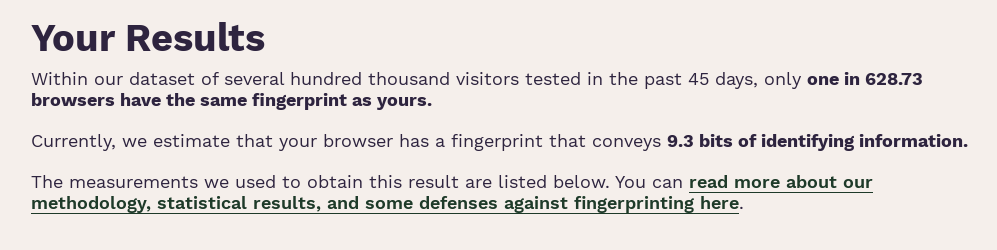
Within our dataset of several hundred thousand visitors tested in the past 45 days, only one in 628.7 browsers have the same fingerprint as yours. Currently, we estimate that your browser has a fingerprint that conveys 9.3 bits of identifying information.
Huh mullvad browser got me the lowest overall. 10.44 bits and a non-unique fingerprint.
Compared against:
- Firefox with arkenfox user.js (macOS)
- Tor (macOS and android)
- Vanadium (android)
- Cromite (android)
- Mull (different than mullvad) (android)
I do a vast majority of my browsing on my phone, unfortunately. Vanadium scored the best (on mobile), but it not having extensions (dark reader is a must) and the navigation bar not being movable to the bottom of the screen keeps me on Mull.
I don't love using mullvad for day to day browsing as I can't whitelist specific cookies to retain. Don't love having to re 2fa daily.
Your browser fingerprint appears to be unique among the 183,996 tested in the past 45 days.
:(
12.67 from Safari/iPhone, without changing any settings. This is my most commonly used browser
Within our dataset of several hundred thousand visitors tested in the past 45 days, only one in 91389.5 browsers have the same fingerprint as yours.
Currently, we estimate that your browser has a fingerprint that conveys 16.48 bits of identifying information
Doesn't look good. How do you make it so that your browser doesn't have a fingerprint at all?
You can't not have a finger print. You can a best try and look like everyone elses.Sadly the free market won't care and as such you won't blend with normal users. Still you can try and look like ever one else in the privacy community
Close it.
How does tails get the bits so low?
Tails uses the Tor Browser which does a lot to minimize fingerprinting, for example by letterboxing so the screen size (one of the most unique information in my case) is rounded as to not be as unique.
16.47 on Cromite. But most of the identify information is not even true, almost everything is spoofed. User agent, timezone, operating system, browser name, screen size and color depth, device, even the battery percentage
Your browser fingerprint appears to be unique among the 183,951 tested in the past 45 days.
Currently, we estimate that your browser has a fingerprint that conveys at least 17.49 bits of identifying information.
well shoot my mobile failed that test lmao
I got 17,49 as well!
I got exactly that number too, but also when I looked at the detailed results section lots of it was incorrect. It got that I was on some sort of Linux and using some sort of FF variant, but things like time zone, plugins, screen resolution and system fonts were all wrong.
So sending out 17.49 bits of largely identifying bullshit is still okay I think lol.
Could it be that the browser shares false information on purpose?
I got 17.5 on my Desktop Firefox lol
with budget vpn on: one in 22756.25 browsers have the same fingerprint as yours
with budget vpn off and just apple safebrowsing on: one in 20231.22 browsers have the same fingerprint as yours.
i have the worst vpn!
A VPN is unrelated, it changes your IP but the IP is not used to fingerprint.
I appreciate the site, but what score is considered good or bad? A cool stat would be some kind of score compared to everyone else.
Vanadium: Your Results Within our dataset of several hundred thousand visitors tested in the past 45 days, only one in 61101.0 browsers have the same fingerprint as yours.
Currently, we estimate that your browser has a fingerprint that conveys 15.9 bits of identifying information.
Default Google Chrome embedded on Android with nothing configured and googled up.
17 bits.
I misread the title as "Cover your taxes" and got really excited to earn about tax avoidance tips. Legal ones obviously.
I get 8.44 bits (1 in 347.34 browsers). I use Firefox with Arkenfox user.js applied on top, with some of my own custom overrides.
However, I think the biggest factor could be because I have Ublock Origin set to medium-hard mode (block 1st party scripts, 3rd party scripts and 3rd party iframes by default on all websites), so the lack of JavaScript heavily affects what non-whitelisted websites can track. I did whitelist 1st-party scripts on the main domain for this test (coveryourtracks.eff.org), but all the 'tracker' site redirects stay off the whitelist.
I actually had to allow Ublock Origin to temporarily visit the tracker sites for the test to properly finish--otherwise it gives me a big warning that I'm about to visit a domain on the filter list.
Best methods to lower the score on android? I tested multiple browsers on EFF. 17 bits regardless of browser.
Interesting, this is a cool test! Unsurprisingly, my setup is rather unique.
One thing that stood out to me is that it failed to detect my adblocker. Also, my screen size alone is unique: 1 in 181697 of this 181697 browsers tested.
What would be considered a high score on this? Is 16 too high?
9.3 bits / 1:628.3
(ipadOS / safari)
...how do they quantify 3/10 of a bit?..
They probably give entropy value, average number of, yes or no, questions that are needed to identify You. (Guess all the information that your browser provided)
After disabling extension "I still don't care about cookies" on Librewolf, I went from 17.48 bits unique fingerprint to 16.48 nearly unique one.
It constantly gives me 17.5 bits on several browsers firefox, nyxt, gnu icecat, librewolf...
If I tried twice and I got a unique id both times, does it mean Firefox is covering my track ?
17.47 on mobile Vivaldi.