Lemmy Shitpost
Welcome to Lemmy Shitpost. Here you can shitpost to your hearts content.
Anything and everything goes. Memes, Jokes, Vents and Banter. Though we still have to comply with lemmy.world instance rules. So behave!
Rules:
1. Be Respectful
Refrain from using harmful language pertaining to a protected characteristic: e.g. race, gender, sexuality, disability or religion.
Refrain from being argumentative when responding or commenting to posts/replies. Personal attacks are not welcome here.
...
2. No Illegal Content
Content that violates the law. Any post/comment found to be in breach of common law will be removed and given to the authorities if required.
That means:
-No promoting violence/threats against any individuals
-No CSA content or Revenge Porn
-No sharing private/personal information (Doxxing)
...
3. No Spam
Posting the same post, no matter the intent is against the rules.
-If you have posted content, please refrain from re-posting said content within this community.
-Do not spam posts with intent to harass, annoy, bully, advertise, scam or harm this community.
-No posting Scams/Advertisements/Phishing Links/IP Grabbers
-No Bots, Bots will be banned from the community.
...
4. No Porn/Explicit
Content
-Do not post explicit content. Lemmy.World is not the instance for NSFW content.
-Do not post Gore or Shock Content.
...
5. No Enciting Harassment,
Brigading, Doxxing or Witch Hunts
-Do not Brigade other Communities
-No calls to action against other communities/users within Lemmy or outside of Lemmy.
-No Witch Hunts against users/communities.
-No content that harasses members within or outside of the community.
...
6. NSFW should be behind NSFW tags.
-Content that is NSFW should be behind NSFW tags.
-Content that might be distressing should be kept behind NSFW tags.
...
If you see content that is a breach of the rules, please flag and report the comment and a moderator will take action where they can.
Also check out:
Partnered Communities:
1.Memes
10.LinuxMemes (Linux themed memes)
Reach out to
All communities included on the sidebar are to be made in compliance with the instance rules. Striker
view the rest of the comments
You download a copy of a photo I took to your computer.
I have a website that lets people see the photo, it's a popular website
Except that photo on my website doesn't point to a copy of that photo on one of my computers, it points to the copy on yours.
Millions of people visit my website, and each time they do, they download your copy of my photo.
Uploading that photo to millions of computers across the world fucks up your internet service. You could also switch out my photo for another one, maybe even an offensive one,, but my website would still point visitors to it.
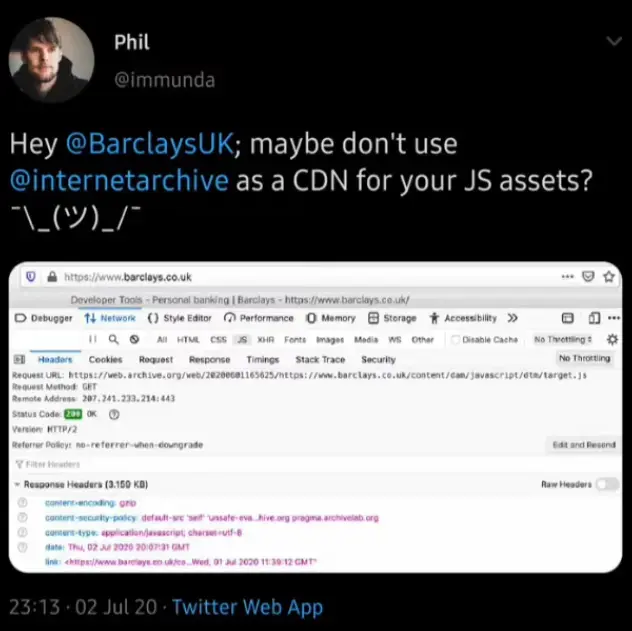
In the original post, this is what a multibillion dollar corporation, a bank, did to a not-for-profit service that keeps a historical record of the internet.
I hinted at the security implications of what happened, but explaining that would make the analogy too complex.
Lets go a little beyond merelly hinting at the security implications:
So people go to the website of a bank and their browser receives code from a 3rd party with whom the bank has no contract and who have nothing in place to obbey the level of security that is required by a banking site.
This is way more "interesting" that the photo from that example of yours (which doesn't have any executable code, only data, being fed to very mature image decoding libraries so it's many times harder to find exploits for it than for code)
Consider the implications of getting the Barclays website to serve (from the point of view of a user) what can easilly be malware...
Fair, although explaining a potential vector for a hypothetical XSS attack and its implications to someone who doesn't know what Javascript is sounds like information overload