this post was submitted on 23 Oct 2024
1873 points (98.6% liked)
Malicious Compliance
19677 readers
3 users here now
People conforming to the letter, but not the spirit, of a request. For now, this includes text posts, images, videos and links. Please ensure that the “malicious compliance” aspect is apparent - if you’re making a text post, be sure to explain this part; if it’s an image/video/link, use the “Body” field to elaborate.
======
-
We ENCOURAGE posts about events that happened to you, or someone you know.
-
We ACCEPT (for now) reposts of good malicious compliance stories (from other platforms) which did not happen to you or someone you knew. Please use a [REPOST] tag in such situations.
-
We DO NOT ALLOW fiction, or posts that break site-wide rules.
======
Also check out the following communities:
[email protected] [email protected]
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
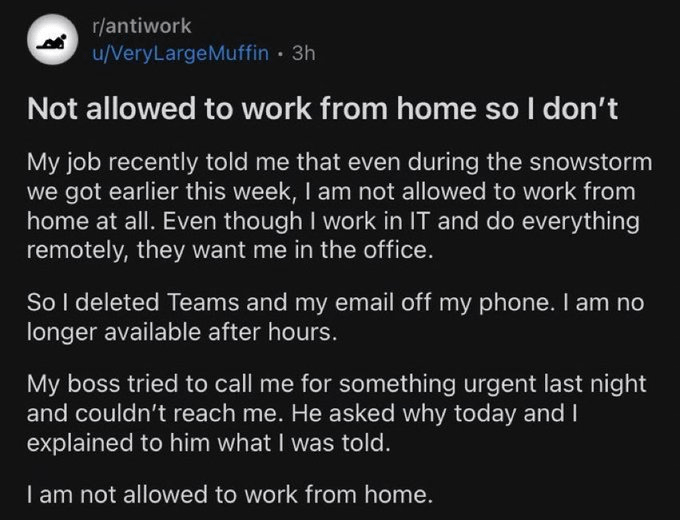
In all of my IT jobs I would have been fired if I had signed into work accounts on my personal phone. It's a pretty big security risk.
True, but in small companies it's not uncommon.
I was at a subsidiary of a very large company and had work slack, email, and all my code on my phone, without even the thing that lets them remote wipe your phone.
It has to do with culture and willingness to put in the effort by the security organization
Get hit with one ransom ware attack and that shit'll pivot 180.
Yeah, or even just budget cuts. I am sure it's cheaper to just lock it down.
Not exclusive to IT; I had to weigh the benefits of continuing to work as a caregiver for a small company, versus working in retail for a massive chain (which translates to fantastic insurance benefits.)
Sadly not a competition.
While true, most enterprises have ways to silo and encrypt their data on non company controlled devices.
Android does something like that when you install ms office apps with administrator controlled policies
Fuck their data, what about my own? That pest of an app is not getting onto my device. And neither is anything else that gives an employer any control over my device.
A totally reasonable stance.
For clarity, the android feature essentially makes a work dedicated partition on the phone. Their management app can manage that partition, and for the purposes of data movement it's essentially a distinct phone.
If they've set it up correctly they can do a remote wipe without touching your personal data.
https://support.google.com/work/android/answer/7502354?sjid=18390510946809838606-NC#zippy=%2Ci-own-my-device
In a lot of cases the drive to have users use their personal devices rather than employer owned ones comes from the users, not the workplace. Only needing to keep track of one device is easier in many cases.
My policy as well. Non-negotiable hard no. But I'm fortunate enough to have at least some choice with regard to employment.
Unless it's 24h gold service with 24k gold pay, the work phone gets turned off at the end of office hours.
There are places that pay well for on call though.
Sounds kinky.
Most companies seem to have don't ask, don't tell policies in place.
Technically we're not allowed to use Teams on our phones, but most of us do, including management.
I'm also technically not allowed to use Spotify on my laptop, but if they'd enforce that ban, IT would be gone tomorrow.
Eh, it doesn't need to be, you just need to do the work of putting together granular access controls that can account for your risk profiles.
The risk isn't much different between a company owned telephone and a personal telephone.
They're both susceptible to most of the same attacks, or being left on the bus.
In my current job the old manager okayed working on our own devices.
I would use my personal workstation to ssh into and do work on my work mac, did that for a few years. saved me disassembling my desk between uses every day or buying a costly KVM.
They seem to be getting a lot more uptight about security these days (although the "you can work on personal devices" rule hasnt been explicitly rescinded) so i have stopped interaction between my personal devices and work devices.
Having a M2 mac recently makes it easier, i can lie in bed and work pretty much all day on a single charge so my desk remains intact
I remote into my work laptop too, but I don't have any work data on my personal devices. And, my desktop is more secure than my work laptop.